The top 5 emerging cybersecurity threats: How to prepare your business in 2025
February 13, 2025

The cybersecurity landscape is constantly changing and cyberattacks are still on the rise, with new threats challenging businesses' defences across Canada. In 2025, we expect some of the new and more sophisticated cyber crimes will include AI-driven attacks, deepfake scams and supply chain attacks.

It’s imperative to understand these threats so that you can better protect your people, customers and ' data, while maximizing the continuity of your operations. Below is a list of the top five cyber threats we believe owners and leaders should watch out for in 2025:
1. AI-driven cyberattacks
Artificial intelligence (AI) and machine learning (ML) are powerful tools for cybercriminals. In 2025, hackers will likely have greater access to AI tools to help automate and enhance their attacks, which could make them increasingly difficult to detect. AI could enable malicious agents to scan networks for vulnerabilities, create highly personalized phishing emails and adapt their tactics in near-real time to evade detection systems.AI-driven attacks are particularly challenging because they require advanced detection tools that can be costly for smaller businesses. Traditional and signature-based security solutions can be less effective against these types of attacks, leaving small and medium-sized businesses (SMBs) more vulnerable to these types of threats. These methods rely on recognizing known patterns or “signatures”, which makes them less capable of identifying new, adaptive threats. Relying on this defence solution alone isn’t enough to safeguard against these evolving cybersecurity risks.
2. Deepfake scams and social engineering
Deepfake technology, which uses AI to create convincing videos and audio to deceive the audience, is advancing rapidly. In 2025, deepfake scams are expected to become a more serious issue as they can help attackers impersonate company executives or trusted contacts in phishing schemes. These deepfake-based social engineering attacks are highly deceptive and can be used to manipulate employees into transferring funds, sharing confidential information or even granting access to a business’ system.These scams pose a unique challenge because they exploit trust within a business. An employee who believes they’re speaking to a senior executive is less likely to question requests, making these attacks particularly more effective.
3. Increased attack surface with remote work
Canadian companies experiencing cloud security incidents cite human error as one of the top causes. With remote and hybrid work models now more common than ever, SMBs face heightened vulnerabilities as employees often connect from personal devices and home networks. These endpoints become attractive targets for attackers, increasing the risk of cybersecurity threats.Insecure connections, lack of visibility and inconsistent security practices can increase difficulty for businesses trying to maintain a secure remote work environment comprehensively.
4. Supply chain attacks
In this type of cyberattack, criminals infiltrate a business by targeting vulnerabilities in its third-party vendors or service providers. Cybercriminals exploit the weakest link in the supply chain, often breaching smaller, less secure vendors to access larger corporate networks. With SMBs frequently connecting to larger enterprises’ systems, they are often seen as easy entry points in the supply chain, putting themselves and their partners at risk.These attacks often result in the distribution of malware through legitimate software updates or services and it can be a challenge for SMBs that may have limited resources to monitor and assess the security of their vendors.
5. IoT-based threats
As connected devices become more ubiquitous, they also become more attractive targets for cybercriminals. SMBs are increasingly relying on the Internet-of-Things (IoT) devices for everyday operations, such as surveillance systems, environmental controls and smart appliances, which can bring a higher risk for attacks that can disrupt operations and compromise sensitive data. Some IoT devices have minimal built-in security, making it easier for hackers to exploit unpatched devices to create botnets, launch distributed denial-of-service (DDoS) attacks or gain unauthorized access to business networks.
The imminent rise of these threats can collectively create a complex cyber environment as they exploit technological advancements, human trust and the expanding digital infrastructure of businesses. To better navigate these threats, businesses should prioritize cybersecurity investments, employee education, regular security assessments, vendor vetting and stay informed about emerging threats.
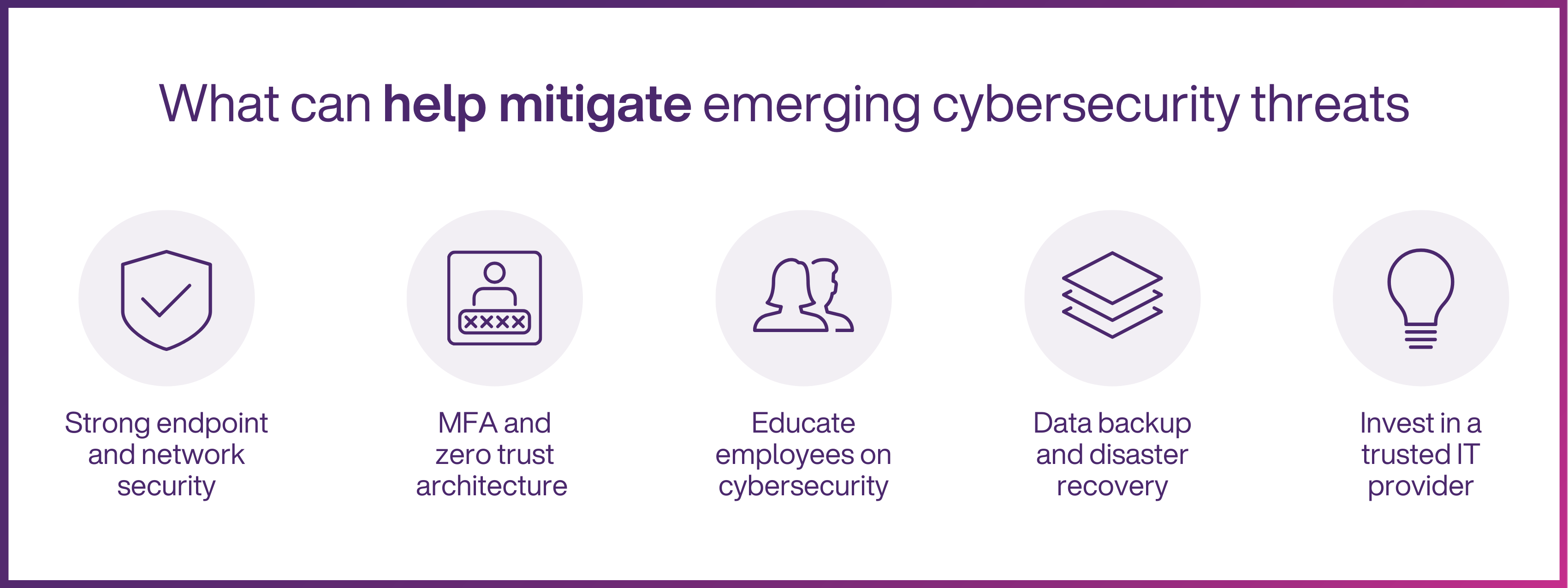
Download the complete checklist to help you protect against emerging and existing cyber threats.
This blog was originally posted on telus.com. To learn more visit telus.com/blog/business.